New firmware on its way
We are now in the process of rolling out firmware version 1.2.0 to all TellStick Net v2, TellStick ZNet Lite and TellStick ZNet Lite v2.
When updating, TellStick may become unresponsive for up to 10 minutes. Please do not turn off or restart your TellStick if this happens.
This update contains about 180 changes. First of all this firmware is prepared for two new features that we are very excited about. "Rooms" is a great way to navigate your devices and will come soon to the new version of Telldus Live! and the app. "Modes" offers completely new possiblities to set up your Events faster and simpler. More information about this will of course follow.
Support is added for some additional sensortypes, for example CO2 and Loudness, and Z-Wave rain sensors.
A much requested feature is the option to now use https in URL event actions.
See http://developer.telldus.com/wiki/FirmwareVersion for a complete changelog.
Firmware 1.1.0 released for TellStick ZNet v1/v2 and TellStick Net v2
We've now released firmware version 1.1.0 for TellStick ZNet Lite v1/v2 and TellStick Net v2. It has some very important new features and bug fixes.
How do I upgrade the firmware?
TellStick will upgrade to the latest version automatically.
It checks for a new version once per day.
If your TellStick has not been upgraded, please just wait. The TellStick will update itself eventually.
If you are experiencing any problems with the upgrade, please contact us at http://support.telldus.com
So what is new in this version?
Plugins for everyone!
The beta for plugins is now available for everyone. Please note that this is still a beta test. There still exists known bugs. Use it on your own risk ;)
Improved support for local control
This firmware includes an improved support for local control which will enable the app to talk directly with TellStick in some cases. This means faster control and the possibility to control your devices even when you do not have an internet connection.
Please note that an internet connection is still required for setup and configuration. The phone must also be connected to the same network as the TellStick.
How do I know if the app uses local control?
The app will show an icon for a house instead of a could if the connection is local.
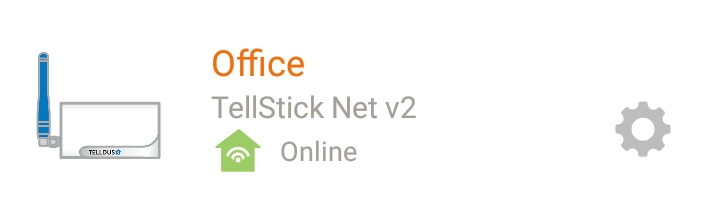
Using local control
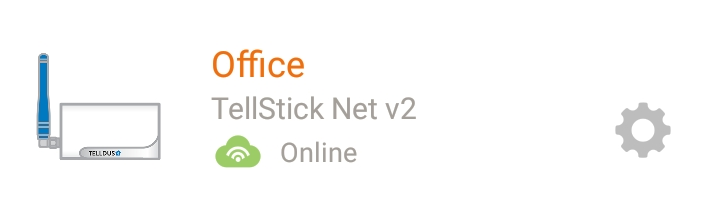
Connected over the cloud
Some buggfixes
For developers
Device type
The api calls device/info and devices/list will now report a new value; deviceType. This value will determine what kind of device it is. So its now possible to easier distinguish between an on/off plug and a door/window sensor in the UI.
For a list of available device types. Please see this list:
https://api.telldus.com/documentation/constDeviceType
Team Telldus
ASUS™ AiProtection reports suspicious networking behavior from TellStick
Some users have been reporting their (ASUS™) routers reports suspicious networking behavior from TellStick. The router alerts that TellStick tries to connect to a suspicious server on the internet.
The alert looks similar to this:
Alert type : Infected Device Prevention and Blocking Source : (AC:CA:54:XX:YY:ZZ) Destination : 193.11.114.43 RT-AC87U’s AiProtection detected suspicious networking behavior and prevented your device making a connection to a malicious website
These types of reports should always be treated seriously. It could be a sign that one of your devices on your network is infected with a malware.
tl;dr
If you aren't interested in the technical description below you can safely ignore this warning. The warning is a false positive.
The technical…
Upon inspection of the captured packets, the IP address reported (193.11.114.43) was not found in the communication of the gateway and the Internet, suggesting the infected source was not on the gateway.
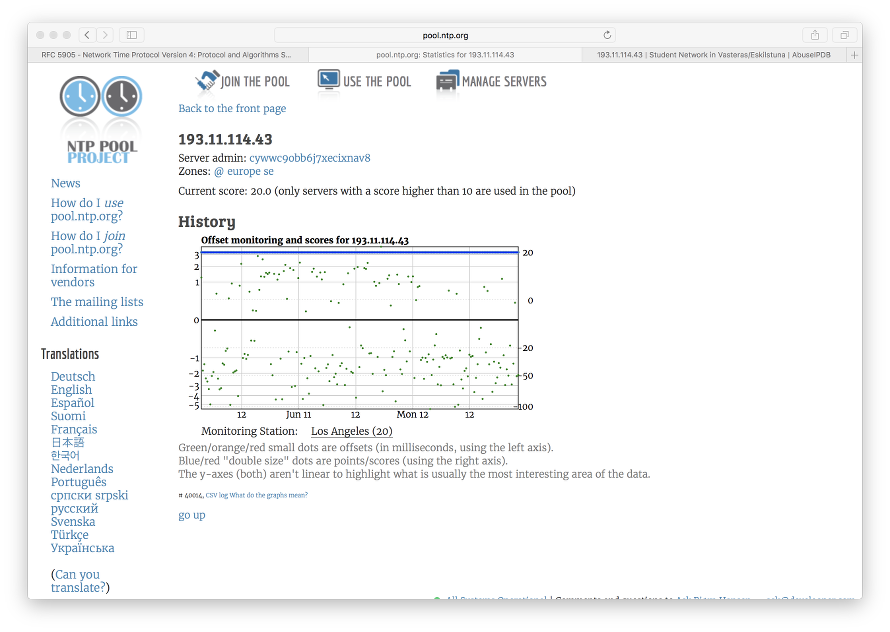
Upon further inspection on the frequent traffic, it was found that NTP accounted for most of the traffic when the gateway is in idle mode. Cross checking with the search results on Google on this IP address indicated it once belonged to the pool of NTP servers under pool.ntp.org.
Querying the IP address via NTP Statistics confirms this IP address was indeed part of the ntp pool machines.
However, a reverse DNS lookup on the same IP yielded a different domain name: tor1.msfnet.se.
root@mangocrap:/var/lib/misc# nslookup 193.11.114.43 Server: 192.168.1.1 Address: 192.168.1.1#53 Non-authoritative answer: 43.114.11.193.in-addr.arpa name = tor1.mdfnet.se. Authoritative answers can be found from:
A DNS lookup in tor1.msfnet.se however revealed no associated IP address,:
root@mangocrap:/var/lib/misc# nslookup tor1.mdfnet.se Server: 192.168.1.1 Address: 192.168.1.1#53 ** server can't find tor1.mdfnet.se: NXDOMAIN
suggesting this is a stale record of the reverse DNS lookup.
The ASUS AiProtection works by querying a third party service (WRS database provided by Trend Micro™) on a suspicious IP address to determine if it is a malicious host.
Looking from this case, it is reasonable to believe either ASUS or Trend Micro uses reverse DNS lookup for the domain name and match it with the list of malicious hosts. In practice, since domain names can be binded to different IP addresses at different time intervals, the IPS mechanism shall not only rely on domain names but also verify using the IP address for malicious host detection in order to reduce false positives.
In conclusion, the IP address that was associated with a malicious web site was being reused as one of the NTP machines in pool.ntp.org for serving network time, the reverse DNS lookup still shows that IP address is being associate with the malicious web site, thus triggering a false positive in the AiProtection mechanism, resulting in the security alert given from the ASUS router. To mitigate, suggest user to report to ASUS on this false positive, and if the router have a whitelist function, add this IP address to the whitelist so that the router will stop generating alerts for this IP address.
Python for TellStick
Did you know that Python can be used to control a TellStick or TellStick Duo?
Our examples show you how to interact with the library directly using ctypes but there is also three third party wrappers to ease the development.
The first one is also based on ctypes but hides the nasty details of the c-library such as memory cleanup. Please check it out: https://bitbucket.org/davka003/pytelldus/
The second one is a native wrapper. This has been merged to our repository here: bindings/python/native
The third one also provides a object oriented interface. Available on github: https://github.com/erijo/telldus-py
So if you are a Python fan, go on and write applications for TellStick using your favourite language.
TellStick on Raspberry Pi
The user davka003 reports that TellStick works fine on his Raspberry Pi. From his blog:
Last friday DHL knocked on my door to deliver a Raspberry Pi. For those that doesnt know what it is, it is a realy small computer running Linux. It didnt took long before I moved over my control software for lamps that uses a Tellstick from Telldus Technologies. Instead of normal light switches I have built in recivers from Nexa that is a remote controlled relay. This make me able to control almost all lighting in the house from anywhere.
Besides playing with my new Raspberry Pi I also built a plastic case to protect it somehow from my sons.
I will post more source code and project details soon on this. But for now have a look at my setup.
Read more on the users blog here: http://automagically.weebly.com/1/post/2012/05/raspberry-pi-how-i-have-longed-for-you.html

 rss
rss